Service Auditing :
Up until now, we have discussed some technology that you can implement to improveyour security. However, a big portion of security is analyzing your systems, understanding theavailable attack surfaces, and locking down the components as best as you can.
Service auditing is a process of discovering what services are running on the servers inyour infrastructure. Often, the default operating system is configured to run certain services at boot. Installing additional software can sometimes pull in dependencies that are also auto-started.
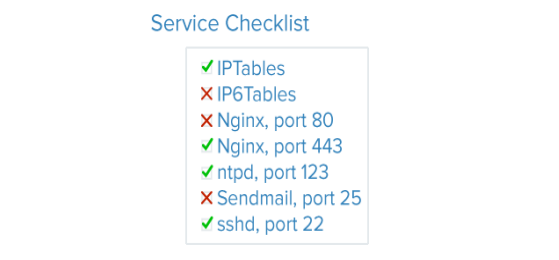
Service auditing is a way of knowing what services are running on your system, whichports they are using for communication, and what protocols are accepted. This information can help you configure your firewall settings.
iMEGH Advantage
OUR VLAUE
24×7 Extended IT Team
We never sleep, so you can
Our always available (24x7x365) enterprise technical support members will act as an extended IT team, helping you to free up your internal technical staff to focus on other important projects
Mitigated Risk
With our enterprise cloud hosting and enterprise support you will gain valuable business continuity and high availability by leveraging our redundant and secure hosting infrastructure
High availability solutions
Agile cloud infrastructure
Experienced enterprise support
Latest hosting technologies